The Evolving Enterprise Risk Surface: Threat Drivers & Dynamics
Enterprises today operate in a hyper-connected digital environment where the pace of innovation is outstripping the capacity of traditional security models to adapt. The rapid adoption of AI, cloud-native architectures, and complex integration layers has erased clear boundaries between systems, data, and users, turning once-separate domains into an interdependent mesh of opportunity and risk. This interconnectedness means that a weakness in one area can quickly cascade across the enterprise, amplifying the impact of a single compromise.
At the same time, attackers are exploiting the very technologies meant to enhance productivity and protection, leveraging automation, machine learning, and sophisticated social engineering to operate at unprecedented speed and precision. Security blind spots, whether caused by fragmented oversight, unmanaged assets, or opaque AI processes, are now persistent fixtures in the threat landscape, often remaining exploitable for weeks or months. The path forward demands technology-specific defenses and tightly integrated security strategies that account for the fluid, ecosystem-wide nature of modern risk.
.png)
- Data Security: Data security has shifted from defending fixed perimeters to protecting sensitive assets in motion across highly distributed, interconnected environments. The erosion of clear trust boundaries, fragmented visibility, and weak control over secrets and third-party integrations has created fertile conditions for high-impact breaches.
- AI Security: AI adoption is reshaping the attack surface, creating opaque operational layers while simultaneously arming adversaries with new offensive capabilities. Without embedded governance and visibility, AI systems can become both a target for exploitation and a tool that accelerates the scale and precision of attacks.
- Identity Security: The integrity of enterprise identity is increasingly under strain from fragmented systems, blind spots in entitlements, and AI-accelerated credential compromise. As identity compromise becomes the pivot point for broader breaches, maintaining continuous trust verification is critical to enterprise resilience.
- Application Security: The modern application stack’s reliance on sprawling APIs and open-source components has magnified its vulnerability footprint. API sprawl, inconsistent controls, and fragile supply chains have created an environment where a single weakness can be silently propagated and exploited at scale.
- Network Security: Enterprise and operational networks have become dynamic, hyper-connected ecosystems where the very tools meant to defend them are now prime attack targets. Long remediation cycles, unmanaged endpoints, and incomplete asset visibility leave persistent footholds for adversaries to exploit.
Data Security
Data security risks have evolved beyond traditional perimeter-based defenses as sensitive assets now traverse diverse and distributed environments, from public clouds to developer pipelines and AI-enabled workflows. The complexity and interconnectivity of these environments have dismantled clear trust boundaries, creating multiple avenues for exploitation. As enterprises contend with both sophisticated external attacks and internal oversights, fragmented visibility, mismanaged secrets, and exposure across third-party integrations are emerging as critical points of failure.
Risk Drivers
Enterprise data security has entered a phase defined by collapsing trust boundaries and unprecedented exposure from the extended digital ecosystem. Sensitive data is no longer confined to hardened internal networks; it flows freely through cloud platforms, CI/CD pipelines, third-party services, and, increasingly, unsupervised AI tools. In this environment, adversaries are exploiting the converging realities of hyper-connected systems, growing data volumes, and fragmented oversight to gain high-impact, persistent access to sensitive, critical, and confidential enterprise data.
- Data Breach Dynamics: Although the global average cost of data breaches declined for the first time in five years during 2025, falling to $4.4 million from a record $4.9 million last year, the financial consequences of breaches remain comfortably above the recent historical annual average. Phishing and third-party-driven compromises represent the most frequent and highest-impact attack vectors, accounting for more than 30% of all breaches and underscoring the rising role of identity- and AI-driven data risks.
- Secrets Sprawl: Poorly managed secrets have become one of the most exploitable weak points threatening data security. Today’s enterprise typically juggles five or more vaulting solutions, yet over three-quarters are misconfigured, and 60% or more contain duplicate credentials across environments. Further accelerating risk is the fact that nearly 40% of tokens are found in unsecured locations like internal tickets or chat threads, with 90% carrying excessive permissions. In this environment, exposed secrets sprawl undermines data security as well as application security.
Risk Mitigation
The evolving risk profile demands that enterprises treat data protection not as a perimeter problem but as a dynamic, ecosystem-wide responsibility. In this environment, enterprises must pair modern data security posture management (DSPM) with advanced data loss prevention (DLP) capabilities to maintain continuous visibility into where sensitive data resides and how it’s being used across cloud, SaaS, and AI-powered environments. By integrating these tools with robust data access governance, enterprises can enforce least-privilege principles, monitor for anomalous access patterns in real time, and apply contextual policies that adapt to the sensitivity of the data and the user’s role.
Highlighted Data Security Innovator – Securiti
Securiti powers a unified, context-aware DSPM platform that bridges data discovery, classification, governance, and AI-sensitive protection. Central to the platform is deep functional coverage across foundational DSPM, DLP, DAG, and related governance controls, delivering deep data end-to-end data protection. Building on a robust data security suite, the platform extends coverage to governance tailored for growing AI environments, including inline LLM firewalls to guard against prompt injection and model-level data sanitization, anonymization, and lineage tracking to help safeguard both AI inputs and outputs. Serving as a centralized and streamlined orchestration command center for data and AI, delivers a unified, AI-aware data security platform that streamlines security and governance across data, AI, and related workflows.
AI Security
AI security risks are evolving on two fronts: the systems themselves and the new attack capabilities they enable. As generative AI, machine learning, and autonomous decision-making become deeply embedded in enterprise operations, they introduce opaque workflows and decision chains that traditional security controls cannot fully observe or audit. Meanwhile, adversaries are weaponizing AI to scale reconnaissance, bypass detection, and craft highly targeted exploits at unprecedented speed. Without robust governance, this dual-use dynamic transforms AI from an innovation driver into a force multiplier for external and insider threats.
Risk Drivers
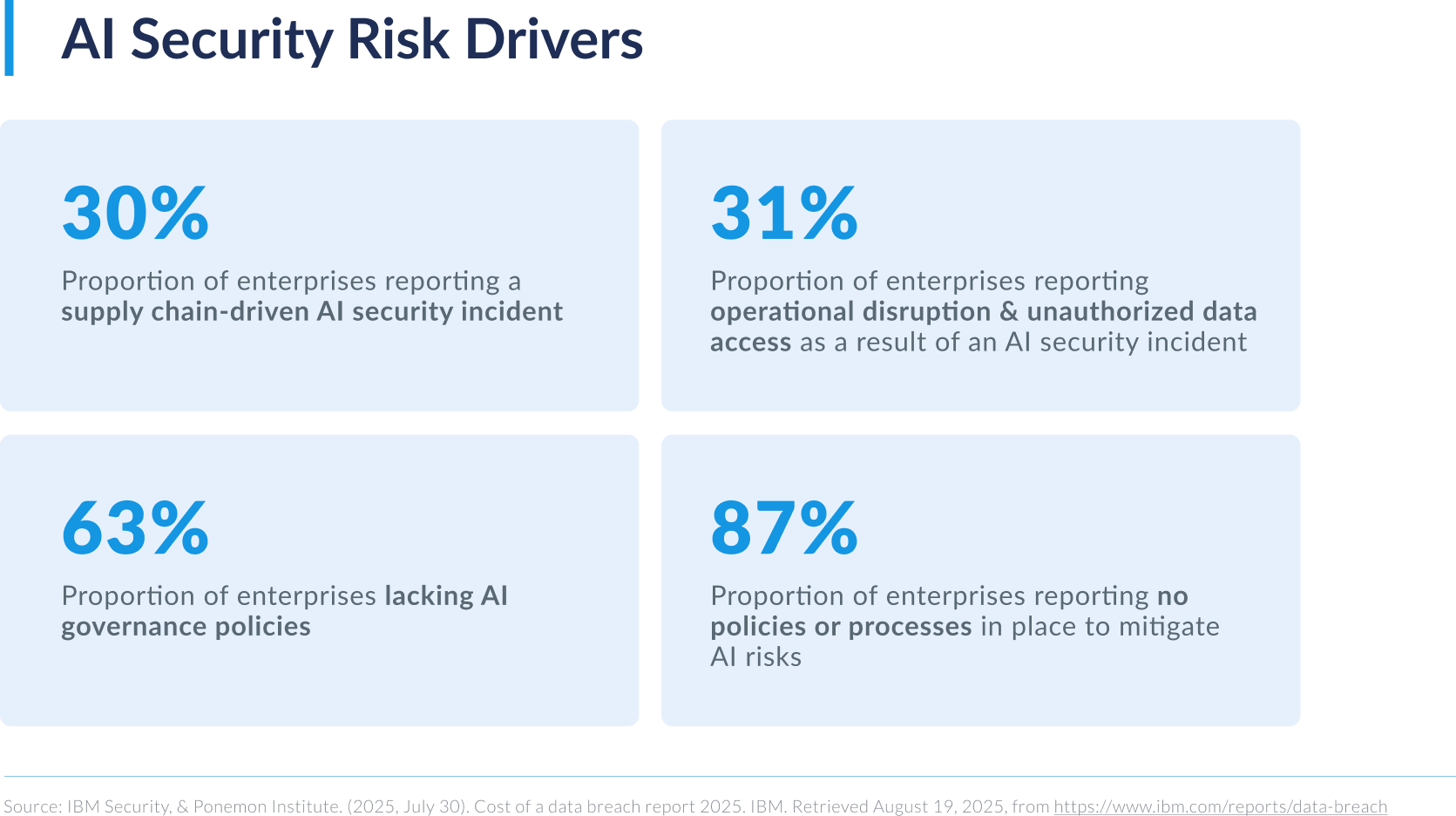
- Advancing AI Risks: Although AI adoption is driving transformative technological advancements and operational improvements, it’s also accelerating the severity, depth, and complexity of the enterprise attack surface. In addition to 20% of enterprises reporting a security breach due to shadow AI incidents, among those reporting an AI data breach or security incident, a whopping 97% indicated the absence of proper AI access controls. Additionally, security incidents involving AI systems are increasingly taking longer to identify, resulting in higher costs and underscoring AI’s growing role as a high-impact attack vector.
- Governance Gaps: Despite the rising threat profile, there is a pervasive lack of meaningful AI governance across enterprises that is exacerbating observability challenges and security risks. Underpinned by the widespread absence of regular model auditing or testing, more than 60% of enterprises lack formalized or institutionalized AI governance policies, and 87% lack any process to mitigate AI risk. These systematic gaps leave enterprises increasingly exposed to exploitable risk and adversarial threats that accumulate with further ungoverned adoption.
Risk Mitigation
The shifting AI threat landscape demands governance and protection that are both purpose-built for AI and embedded into enterprise security operations. Enterprises should integrate AI-specific access controls, model usage monitoring, and behavioral anomaly detection to prevent unauthorized use and data leakage. Equally important is operationalizing AI governance, including embedding model validation, adversarial testing, and risk reviews into MLOps pipelines, all of which ensure adoption is matched with continuous oversight and resilience.
Highlighted AI Security Innovator – Fiddler
As a purpose-built AI observability platform, Fiddler integrates with production ML and LLM pipelines to deliver enterprise-grade security, explainability, and governance. Combining latency-conscious monitoring, root-cause diagnostics, and compliance alerts across AI model behavior, Fiddler facilitates deep monitoring, bias detection, and root-cause diagnostics for ML models, LLM deployments, and AI agents. Alongside guardrails and prompt-level monitoring of hallucinations, toxicity, and PII leakage, Fiddler affords end-to-end observability-based security for AI model and workflows.
Identity Security
Identity has become the connective tissue of enterprise security, and its failure can unravel defenses across the stack. Fragmented identity infrastructures, siloed directories, and limited entitlement visibility create fertile ground for privilege abuse, whether intentional or opportunistic. As AI-enhanced phishing and credential theft accelerate the pace of compromise, the stakes grow higher: a single breached identity can unlock pathways to sensitive data, critical applications, and core infrastructure.
Risk Drivers
- Identity Fragmentation: Through 2025, identity security remains perilously fragile, hamstrung by fragmentation and blind spots that attackers are all too eager to exploit. A resounding 70% of enterprises note that identity silos constitute a root driver of cyber risk. This fragmentation plays a critical role in eroding trust and visibility, illustrated by the fact that 49% of enterprises still lack visibility into permissions across their cloud environments, creating fertile ground for privilege creep and entitlements drift.
- AI Accelerated Identity Threats: Adversarial integration of AI tooling has driven an unprecedented advancement of identity-based threat velocity, sophistication, and frequency. Compromised credentials and phishing represent two of the four most costly breach vectors, the former of which experienced a 160% rise in frequency compared to last year and the latter of which has emerged as the most frequent source of all data breaches. Additionally, there has been a notable rise in the risk of insider threats, with malicious insiders representing the most costly data breach attack vector and the growing threat of unintentional AI-driven data leakage further underscoring the high dimensionality of identity security.
Risk Mitigation
Addressing identity risk requires consolidation, visibility, and adaptive control. Organizations should unify identity systems and integrate them tightly with security operations to enable centralized entitlement management, real-time risk scoring, and automated policy enforcement. To blunt the impact of compromised credentials, enterprises should also prioritize modernized and phishing-resistant MFA, continuous authentication, and behavior-based anomaly detection. With this approach, enterprises can ensure that identity trust is constantly verified, not assumed, to reinforce an adaptive, resilient, and holistic zero-trust-based security posture.
Highlighted Identity Security Innovator – Veza
Veza transforms identity governance with its authorization graph, which maps permissions across human and machine identities in hybrid, cloud, and SaaS systems to support full lifecycle management, from provisioning to access review. Translating disparate access metadata into a single control plane, the platform enables continuous discovery and remediation of privilege entitlements, granular identity policy enforcement, and lifecycle automation.
This model-centric approach streamlines scattered permissions and disparate security tools within a single control plan, eliminating dependence on exploitable legacy or siloed architectures.
Application Security
Modern application ecosystems are living systems, constantly shifting through API integrations, code dependencies, and software supply chain updates. This dynamism enables agility and innovation but also invites complexity, making it easier for shadow APIs, misconfigured endpoints, or tampered code to slip past oversight. The sheer scale of API interconnections and open-source reliance means vulnerabilities can propagate quickly across environments, often without immediate detection. As the application attack surface becomes more modular, so too does its susceptibility to both targeted exploitation and collateral compromise.
Risk Drivers
- API Acceleration: The modern enterprise application stack is increasingly API-driven, with nearly half of applications now relying on 26–50 APIs, on average, a figure rising steadily alongside microservices adoption and external AI integrations. The challenge and difficulty in effective API observability and management is compounded by 36% of enterprises manage more than 1,000 APIs, creating substantial governance and security complexity. This API sprawl, often paired with incomplete inventories, leads to shadow APIs, inconsistent authentication policies, and exposure of sensitive data through improperly validated endpoints. In this environment, adversaries increasingly exploit these weaknesses through injection attacks, credential stuffing, and business logic abuse.
- Software Supply Chain Fragility: The GitHub supply chain compromise in March 2025 demonstrated how a single exposed automation token could cascade into 23,000 compromised repositories. With the average enterprise relying on over 180 open-source components per application, most of which lack software bills of materials (SBOMs), visibility into code provenance is dangerously thin. The result is a persistent risk of malicious code injection, dependency confusion, and tampered updates slipping into production environments undetected.
Risk Mitigation
Application security resilience starts with observability and trust enforcement across every integration point. Enterprises should maintain a dynamic, continuously validated API inventory, applying consistent authentication, authorization, and schema validation at both design and runtime. To address software supply chain fragility, there must be a focus on enforcing SBOM requirements, applying dependency pinning, and integrating integrity verification directly into CI/CD pipelines.
Highlighted Application Security Innovator – Apiiro
Apiiro’s Application Security Posture Management (ASPM) platform converges AppSec and software supply chain security (SSCS) into a single pane of glass, delivering extended SBOM (XBOM)-based visibility, native code and CI/CD scanning, integrated risk graphs, and deep context-aware prioritization. The platform integrates API-level and supply-chain insights with contextual analysis, resulting in embedded, streamlined, and prioritized risk remediation within developer pipelines.
.jpg)
Network Security
The enterprise network is no longer a fixed perimeter, but an evolving mesh of physical, virtual, and cloud-connected assets. Attackers have adapted by targeting the very technologies that were once considered its strongest safeguards, from firewalls to VPNs to IoT-enabled edge devices. Long patch cycles, unmanaged endpoints, and incomplete asset visibility leave openings that can persist for months, offering adversaries a durable foothold inside operational and corporate environments. With this shifting topology, the network has become both a conduit for business and a hotly contested domain characterized by rising vulnerability exploitation.
Risk Drivers
- Last year, 44% of zero-day exploits targeted enterprise technology, up from 37% the prior year, more than 60% of which specifically targeted security and networking products, marking a pivotal shift where tools built to protect the enterprise have become primary entry points. Further, identified vulnerabilities in edge and VPN appliances have surged eightfold, yet only 54% are patched, with a median remediation time of 32 days.
- The network risk landscape is even more dire across critical infrastructure operators, with more than 60% of identified IoT vulnerabilities remaining unpatched for more than six months after disclosure. When combined with the fact that a notable majority of enterprises lack a unified inventory of connected devices, many of which rely on default credentials, these prolonged windows and visibility gaps create a persistent, high-value pool of exploitable ingress points across operational and enterprise networks.
Risk Mitigation
Securing modern networks requires both accelerated remediation and deep asset intelligence. Enterprises should adopt automated vulnerability prioritization and patch orchestration for network infrastructure, with compensating controls in place when immediate remediation isn’t possible. Equally critical is establishing a unified inventory of all connected assets, enforced with zero-trust segmentation, strong authentication, and continuous monitoring, to ensure that exploitable ingress points are identified, hardened, and isolated before they can be used for compromise.
Highlighted Network Security Innovator – Pomerium
Pomerium is a lightweight and modernized VPN replacement, comprising an application-layer ZTNA proxy that continuously verifies identity, context, and device posture before granting access. By directly integrating identity-aware access policies and authentication mechanisms into routing decisions, Pomerium allows enterprises to secure internal and cloud-hosted applications without exposing them to the public internet, thereby reducing the network attack surface and lateral movement risk.
Conclusion
The evolution of the enterprise risk surface signals a decisive turning point in security strategy. As adversaries exploit the interconnected nature of data, identity, applications, AI systems, and networks, reactive and siloed approaches are proving both insufficient and unsustainable. In the modern environment and landscape, threats move fluidly across technology layers, meaning a vulnerability in one domain can quickly and easily cascade into systemic compromise across the enterprise.
Enterprises must now adopt an integrated, intelligence-driven posture that treats each domain not as an isolated asset, but as part of a living, interdependent security ecosystem. This requires embedding governance, observability, and adaptive controls directly into core systems, ensuring visibility and resilience are inherent capabilities rather than afterthoughts. At Vation Ventures, we help organizations design and operationalize these interconnected security strategies, whether it be fortifying architectures, streamlining governance, and enabling proactive risk management. Our approach equips leaders with the insights and capabilities needed to defend at the speed of modern threats. Contact us today to future-proof your security strategy.




